- Home
- Solutions
- Products
- Security Management SolutionsASIS Technologies designs and manufacture a comprehensive range of software for access control applications. All the software is compatible to ASIS Technologies hardware products. Application with GUI feature to make it much more user-friendly for database setting and viewing report.
- Security Management SolutionsASIS Technologies designs and manufacture a comprehensive range of software for access control applications. All the software is compatible to ASIS Technologies hardware products. Application with GUI feature to make it much more user-friendly for database setting and viewing report.
- Hardwares
- Access ReadersASIS Technologies designs and manufactures a comprehensive range of readers for access control applications. All readers are housed in elegant, industrially designed casings and come with options for keypad, LCD display, SAM (Secured Access Module), Wiegand and RS485 communication interface.
- IP Access ControllersASIS Technologies designs and manufactures a comprehensive range of controllers for access control applications. All controllers act as storage for user data and event transactions. It running either with RS485/TCPIP communication signal.
- CredentialsSmart cards are cards that are embedded with either a microprocessor and a memory chip or only a memory chip with non-programmable logic. The microprocessor card can add, delete, and otherwise manipulate information on the card, while a memory-chip card (for example, pre-paid phone cards) can only undertake a pre-defined operation. Smart cards, unlike magnetic stripe cards, can carry all necessary functions and information on the card. Therefore, they do not require access to remote databases at the time of the transaction. Integrated Circuit (IC) Microprocessor Cards (generally referred to as “chip cards”) offer greater memory storage and security of data than a traditional mag stripe card. Chip cards also can process data on the card.
- Video Surveillance SolutionsASIS Technologies offers a wide range of high-resolution megapixel IP cameras with options from dome, all-in-one (bullet) and PTZ cameras.
- Crowd Management EquipmentASIS Technologies have a comprehensive range of turnstiles for access control applications. This including flap barrier, tripod, drop arm, swing door and full height turnstiles.
- Access Control AccessoriesIntegration among various subsystems is a hallmark of solutions offered by ASIS Technologies. Our Products are designed with built-in, advanced capabilities to ensure seamless integration between Electronics Access Control, Contact-less Smart card, CCTV Surveillance and Crowd Management systems. With our many years of experience and integration capabilities, our integration solutions make our operating console the master Command & Control Centre for the entire facility/premises.
- Resources
- Partners
- About
Advanced Audit Report (AAR)
Enhance IBSSweb security with the Advanced Audit Report. Track detailed changes, user activity, and permissions for accountability in financial, government, and high-security sectors.
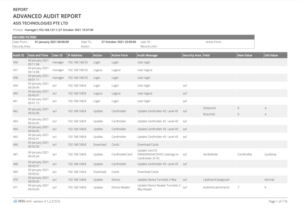
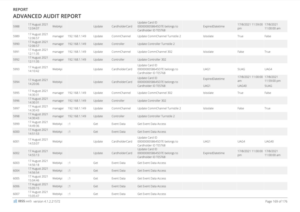
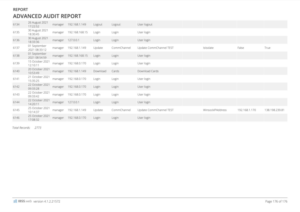
The AAR goes beyond basic access logs. It captures a detailed field-by-field change log, allowing you to pinpoint even minute modifications made by individual users. This in-depth insight is crucial for investigations, compliance, and maintaining a secure environment.
With the AAR, you can:
- Trace Individual Actions: See precisely who made what change, when, and from where.
- Investigate Permissions: Uncover who granted access or modified permissions, ensuring accountability.
- Monitor System Integrity: Quickly identify unauthorized changes or suspicious activity.
- Meet Compliance Requirements: Maintain comprehensive audit logs for regulatory compliance.
- Enhance Security: Deter unauthorized actions and strengthen your overall security posture.

Key Features
- Detailed Field-by-Field Change Log: Track modifications at the most granular level.
- Individual User Activity Tracking: See exactly who did what within the system.
- Permissions Management Audit: Monitor changes to user permissions and access levels.
- High Accountability Focus: Designed for critical industries with strict security requirements.
- Comprehensive Reporting: Easily generate audit reports for analysis and compliance.
- Seamless IBSSweb Integration: Install and configure effortlessly as an add-on module.
| Specifications | IBSSweb-AAR |
| Description | IBSSweb Advanced Audit Report |
| IBSSweb Versions | IBSSweb Professional Edition or above (Prerequisite) |
| Supported Operating System | Windows 10 (64bit) / Windows Server 2016 or above |
| Total Records | Unlimited |
| Export Formats | PDF, XLS, XLSX, PPT, RTF, TIFF, MHTML, DOCX, XPS |
*Specifications are subject to change without prior notice
Datasheet: https://www.asis-technologies.com/datasheets/software-datasheets/
| Model No. | Description |
| IBSSweb-AAR | IBSSweb Advanced Audit Report |
RELATED PRODUCTS
Related products
-
WebAPI (API)
Web API is an add-on module of IBSSweb that opens an interface between third party devices & services and the…
-
Report Generator (RPG)
Report Generator is an IBSSweb add-on module which offers flexibility in creating reports using the IBSSweb database. Originally designed as…
-
Messaging Gateway (SMS)
Messaging Gateway is an add-on module that gives IBSSweb users real-time notifications arising from events and/or alarm events, enhancing operational…
-
Secret Key Management System (SKeyMa)
It is an integrated approach for managing secret key, personalise Secure Access Module (SAM), readers and also contactless card.